Toshiba Information Systems (Japan) Corporation
The hardware Trojan detection service
Recently, we concern about the risk of the hardware Trojan embedded in some IC chips as a malicious circuit.
The hardware Trojan causes operations that the user does not expect. Toshiba Information Systems (Japan) Corporation has developed a tool to detect hardware Trojan embedded in the circuit design process, HTfinder, jointly with Waseda University.
The scope of the hardware Trojan detection service is design data of semiconductor circuit. Any completed LSIs or products themselves that use LSIs including information equipment, automobiles, home appliances can not be applied.
This service is for domestic customers only.
The hardware Trojan
The Trojan is malware (program that attacks the computer system when receiving a trigger). The hardware Trojan is the hardware version of the Trojan.

The hardware Trojan is embedded by a malicious third party in the LSI design process. Once it starts an attack by the set up trigger, the attack is not stoppable. The hardware Trojan is difficult to find through general simulation or other means because it can be neatly embedded in an encrypted chip or wireless module. Therefore, you need a special detection process to check that hardware Trojan are not mixed in before manufactureing.
Threat of the hardware Trojan
High density, high speed, multifunctional are required for LSIs to support smart devices that are smaller and more powerful. As a result, only a few manufacturers now internally perform design through manufacturing semiconductor. They usually outsource some design processes or use third-party's intellectual property.
In this increasingly complicated design process, unauthorized circuits are more likely to be embedded than before. In this smart society era, hardware can also cause a various types of damage, including leakage of important information, or the spread of viruses in many areas.
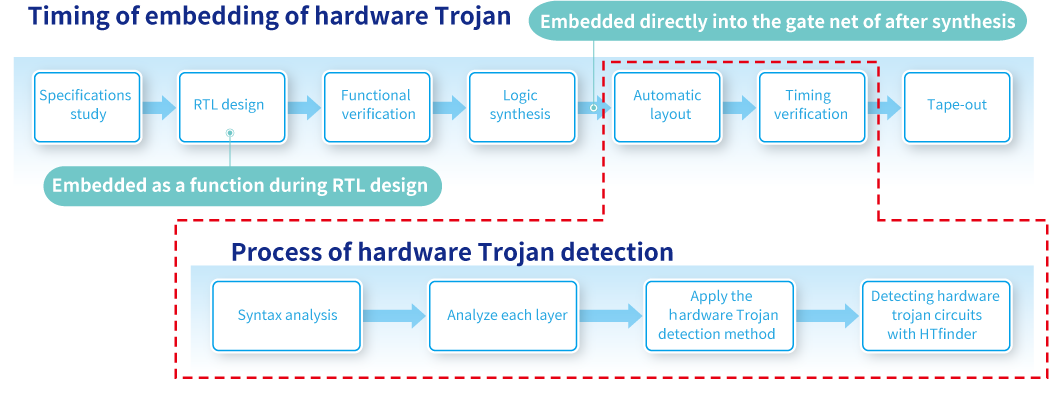
The hardware Trojan detection

To detect a hardware Trojan, you find some characteristics that can indicate a hardware Trojan in the circuit structure (weak identification) and score them (strong identification) to determine if they suggest a hardware Trojan in a comprehensive way. We checked if the tool is capable of detecting hardware Trojan in a gate net equivalent to an actual circuit data while researching data published by Trust-HUB, the standard hardware Trojan benchmark, to improve the detection accuracy of HTfinder.
Most hardware Trojan are extremely difficult to detect during the circuit operation check of IC chips because they are designed to operate only when a specific symbol is input. We believe that we must quickly set up an environment where semiconductor manufacturers can safely outsource design to subcontractors as well as an environment to check for hardware Trojan during semiconductor development so that end users can safely use products.
The hardware Trojan detection service
Currently we provide a hardware Trojan detection service using HTfinder. Please take this opportunity to consider using our service.
- Identify circuits that could be exploited in semiconductor circuits.
- Technical partnership with Togawa Laboratory at Waseda University.
We have applied the hardware Trojan detection method of the Laboratory.
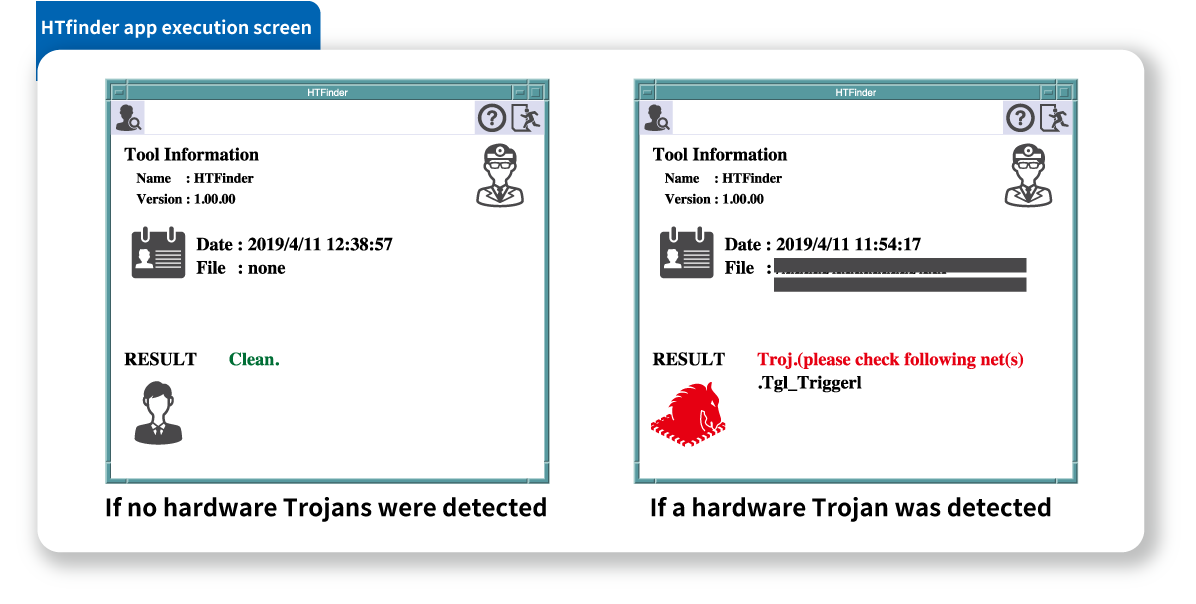
Toshiba Information Systems (Japan) Corporation provides the hardware Trojan detection service to detect hardware Trojan and their possibility using HTfinder, a tool based on the pattern matching method. The hardware Trojan detection service reports whether there are threats and grounds for the decision based on the detection result output from HTfinder.